
Doctrine for Continuity, Sovereignty, and Decision Assurance in the Digital Age
Modern nations no longer fail solely due to physical catastrophe.
They fail when digital systems lose integrity, continuity, or command authority under pressure.
National Digital Resilience is the ability of a state, sector, or sovereign institution to:
• Maintain control of digital territory during disruption
• Continue essential functions despite cyber, AI, or hybrid attack
• Make trusted decisions when identity, data, or infrastructure is degraded
InterOpsis™ addresses this problem at the doctrinal level, not as a tool, product, or service.

A Doctrinal, Not Operational, Approach
InterOpsis™ is governed by the Cybersecurity Constitution™, a sovereign‑grade doctrine that establishes enforceable authority over digital systems, identity, data, and interoperability.
It is not:
• A cybersecurity product
• An implementation contractor
• A managed service
• A compliance framework
It is:
• A governing doctrine for national‑scale digital resilience
• A readiness and assurance system
• A constitutional model for survivability, control, and continuity
All operational execution remains with the adopting organization or state.
InterOpsis™ provides doctrinal authority, readiness validation, and assurance artifacts.

From Cybersecurity to National Resilience
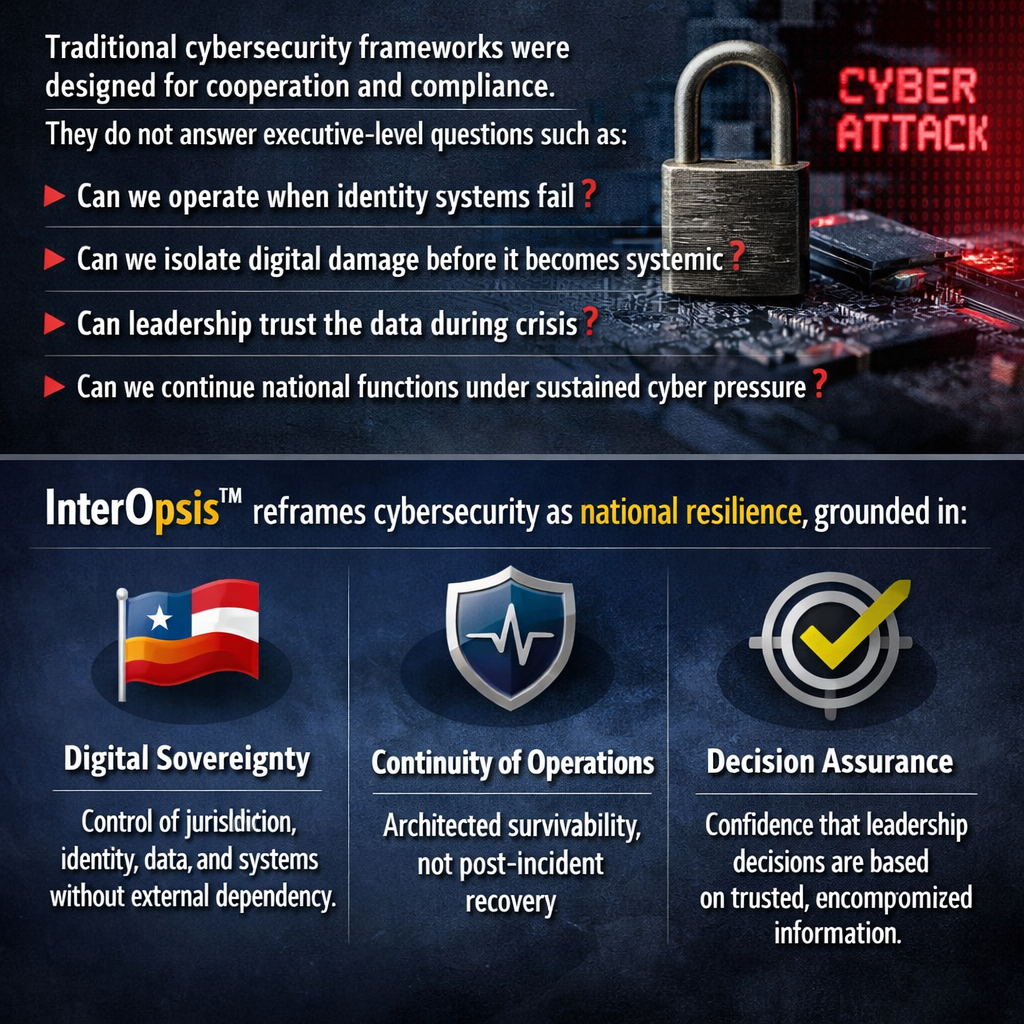
Traditional cybersecurity frameworks were designed for cooperation and compliance.
They do not answer executive‑level questions such as:
• Can we operate when identity systems fail?
• Can we isolate digital damage before it becomes systemic?
• Can leadership trust the data during crisis?
• Can we continue national functions under sustained cyber pressure?
InterOpsis™ reframes cybersecurity as national resilience, grounded in:
• Digital Sovereignty
Control of jurisdiction, identity, data, and systems without external dependency.
• Continuity of Operations
Architected survivability, not post‑incident recovery.
• Decision Assurance
Confidence that leadership decisions are based on trusted, uncompromised information.
Readiness Is Proven, Not Assumed
National resilience cannot be declared. It must be demonstrated.
InterOpsis™ includes SecureTrain™, a doctrine‑enforced exercise and readiness system designed to validate:
• Continuity under simulated cyber and infrastructure disruption
• Command and escalation pathways
• Identity and data integrity under stress
• Cross‑domain isolation and recovery
• Executive decision‑making with degraded systems
SecureTrain™ is not “training.”
It is a national‑scale readiness and assurance mechanism

Assurance Artifacts for Executive Consumption
Each doctrinal exercise produces assurance artifacts, not technical reports.
These artifacts are designed for senior leadership and national‑level stakeholders and may include:
• Readiness and survivability assessments
• Evidence of isolation and containment
• Continuity validation results
• Restoration and reconstitution outcomes
• Decision‑support integrity under pressure
These outputs are consumable at the policy, strategy, and national coordination level without exposing sensitive operational detail.

Non‑Implementing, Non‑Operational Posture
InterOpsis™ does not operate systems, deploy tools, or assume control of environments.
Its role is to:
• Define sovereign digital doctrine
• Validate readiness through exercises
• Produce assurance artifacts
• Preserve authority, ownership, and control with the adopting entity
This posture ensures compatibility with:
• Government agencies
• Defense and intelligence organizations
• Critical infrastructure sectors
• National and multinational coordination bodies

National Resilience Starts With Doctrine
Technology changes.
Threats evolve.
Doctrine endures.
National Digital Resilience is not achieved by adding more tools.
It is achieved by establishing sovereign authority, enforceable readiness, and trusted decision‑making in the digital domain.
InterOpsis™ exists to provide that foundation.

Designed for National‑Scale Environments
InterOpsis™ doctrine has been developed for environments where failure is unacceptable, including:
• National security and defense ecosystems
• Critical infrastructure and lifeline sectors
• Cross‑agency and cross‑domain systems
• AI‑enabled and hybrid threat landscapes
It is intentionally incompatible with superficial compliance models and resistant to external control vectors.

